A shocking 81% of organizations had sensitive data exposed in the cloud. It’s a breach-in-waiting with catastrophic consequences. From an impact on business continuity and loss of customer trust to regulatory fines and a jolt to your brand, the consequences can be devastating.
Moreover, if your organization handles personally identifiable information (PII) or sensitive information such as financial data, credit card numbers, health records, or social security numbers.
To help protect sensitive data and mitigate the risk of data loss, Microsoft offers a helpful set of data loss prevention (DLP) policies. In this blog we will detail how you can improve security with Microsoft 365 Data Loss Prevention. Identify, monitor, and automatically protect sensitive items across Microsoft 365 services such as Teams, Exchange, SharePoint, and OneDrive using these Microsoft 365 DLP policies.
What is Microsoft 365 Data Loss Prevention
Data loss prevention (DLP) is a vital security practice that prevents your organization from losing sensitive data. It is crucial to secure your data from internal leaks, external threats, and accidental disclosures. Microsoft provides an excellent solution for data loss prevention with Office 365. With Office 365 DLP, you can protect your confidential data by creating policies and rules that detect, monitor, and take action against unauthorized access and sharing of your data.
How to Setup Microsoft Office 365 Data Loss Prevention
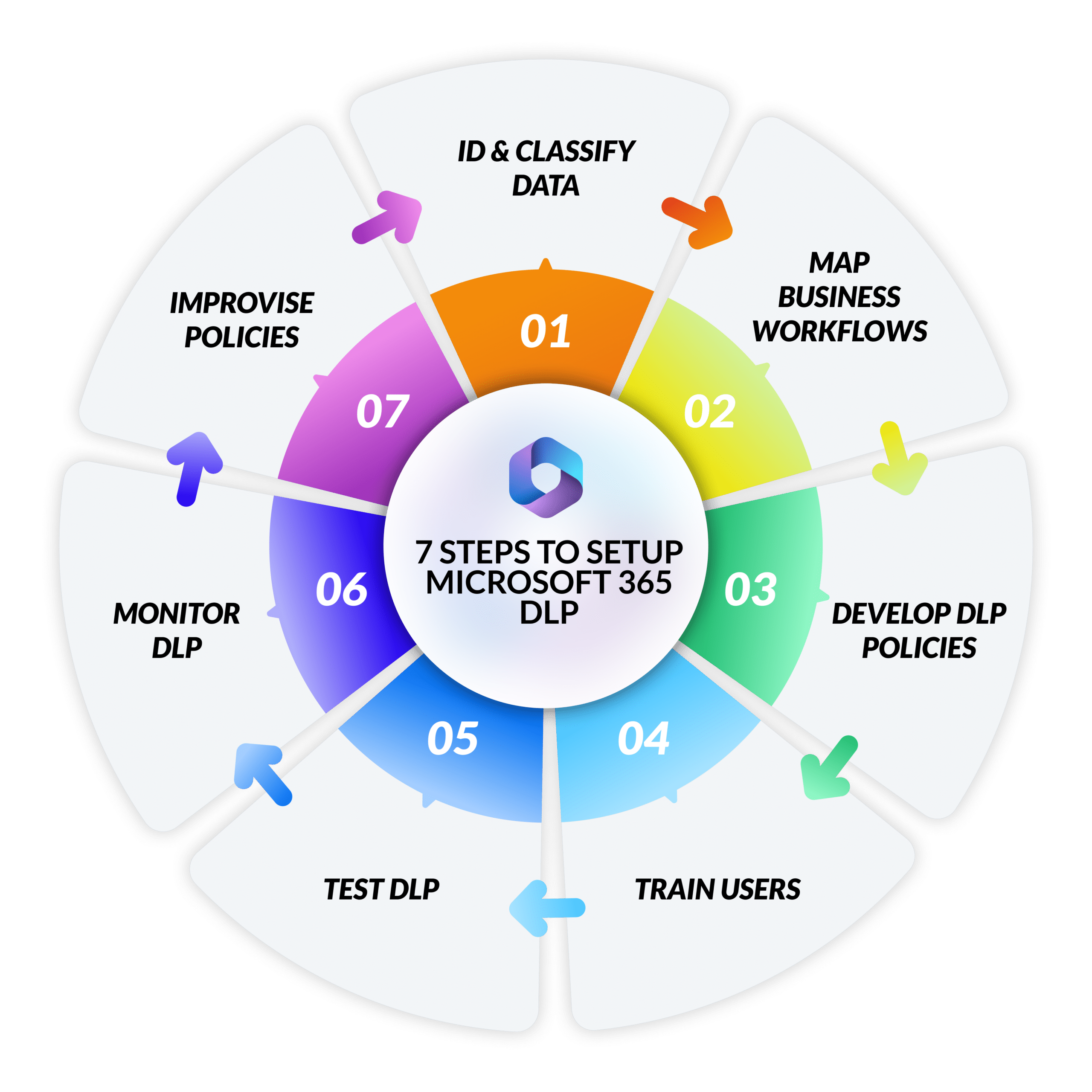
7 Steps to Setup Microsoft 365 Data Loss Prevention
Step #1: Identify and classify sensitive data for M365 DLP
The first step towards setting up Office 365 DLP is identifying and classifying sensitive data. You need to know what type of data you have and where it is located. Microsoft provides a set of predefined sensitive information types that can help you identify sensitive data in your organization. You can also create your own custom-sensitive information types to match the specific needs of your organization. Once you have identified your sensitive data, you can classify it based on its level of sensitivity and importance.
Step #2: Work with business owners to map workflows for Microsoft 365 DLP
Implementing Data Loss Prevention (DLP) policies can prevent prohibited activities, such as the sharing of sensitive information through email. When creating your DLP policies, it’s important to determine which business processes involve your sensitive items.
Working with business process owners can help you identify acceptable user behaviors and those that should be prevented. This way, you can establish DLP policies that are tailored to your organization’s unique needs and effectively safeguard your sensitive information.
Additionally, policies can be configured to show pop-up warnings when users are attempting to share sensitive data in an unauthorized manner, giving employees the option to override the warning with a justified reason or blocking the sharing altogether. For data at rest, DLP policies can also lock and move sensitive items to a secure quarantine location or prevent them from being displayed in Teams chats.
Step #3: Create Office 365 Data Loss Prevention policies
After identifying and classifying your sensitive data, the next step is to create DLP policies. DLP policies are rules that specify what actions to take when sensitive data is detected. With Office 365 DLP, you can create policies that monitor and prevent the unauthorized sharing of sensitive data through emails, documents, and other communication channels. You can also customize policies based on your organization’s unique requirements. Here are pointers to create Office 365 DLPs.
Microsoft Information Protection also provides a complete set of tools for data labeling and classification that uses Artificial Intelligence and Machine Learning to ensure adherence to both internal sensitive information policies and external regulatory requirements.
By offering over 100 types of sensitive information and 40+ pre-built policy templates for commonly accepted industry standards, MIP enables a fast and efficient solution for achieving compliance. For instance, you can create d
ifferent policies for different departments, such as HR, Finance, or Legal. DLP provides a whole host of templates for various categories such as Financial, Medical, and Piracy.
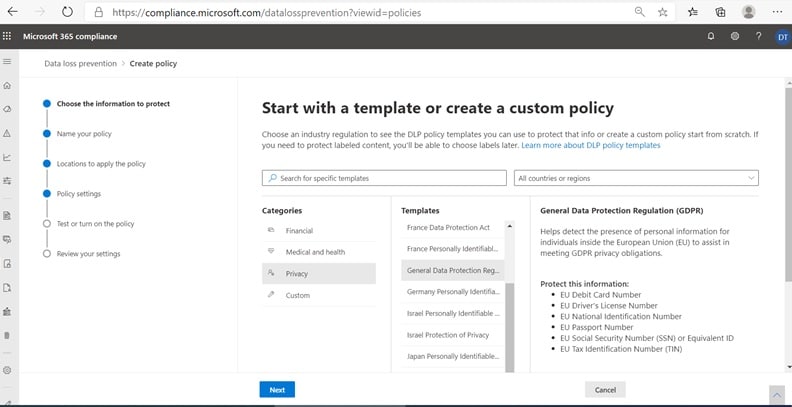
Microsoft Office 365 Data Loss Prevention Policy Templates
Step #4: Train Users and Evangelize Microsoft 365 DLP policies
To maximize the effectiveness of Microsoft 365 DLP policies, the next crucial step is to train your users and evangelize the policies within your organization. User education should involve comprehensive training sessions that explain the importance of data protection and the role of DLP policies in preventing data leakage. Make sure to give clear examples of potential security risks and the consequences of data breaches.
Furthermore, consider creating easy-to-understand materials like infographics, cheat sheets, or short video clips to illustrate the dos and don’ts of handling sensitive data. This will help your users grasp the concept more effectively and make them aware of their individual responsibilities in safeguarding the organization’s data.
Evangelize your DLP policies by communicating and promoting them at all levels within the organization. This can be done through regular newsletters, emails, webinars, or town-hall meetings. Make it a point to stress that everyone’s cooperation and adherence to these policies contributes significantly to the overall security of the organization. The goal is to cultivate a data-conscious culture where every user understands, respects, and adheres to DLP policies.
Step #5: Test and refine Microsoft 365 DLP policies
Once you have created Microsoft 365 DLP policies, the next step is to test and refine them. Test your policies by simulating different scenarios that might trigger a policy violation, such as sending an email containing sensitive data to an external recipient.
You can also deploy them in test mode, and assess their impact using the activity explorer before applying them in more restrictive modes. Refine your policies based on the feedback and experience of your users. Collect feedback from users who receive policy violation alerts and adjust policies accordingly to avoid false-positives.
Step #6: Monitor Office 365 DLP policy violations
The final step in setting up Office 365 DLP is monitoring policy violations and taking action. You can use the reporting and analytics tools in Office 365 to track policy violations and analyze trends. You can also configure alerts and notifications to inform you and your IT team when policy violations occur.
Depending on the severity of the policy violation, you can take different actions, such as blocking access to sensitive data, revoking permissions, or quarantining data for further investigation.
Microsoft 365 DLP also provides robust reporting capabilities to gain valuable insights into how data is being used and if any policy violations have occurred such as:
- The DLP Policy Hits over Time report illustrates the number of times your DLP policies have been triggered over a specific period. This can help you identify any spikes in policy hits, which may indicate a potential security threat or an area where additional user training is needed.
- The Top Sensitive Information Types report shows which types of sensitive information are most commonly found in your data. This information can guide you in fine-tuning your DLP policies and focusing your protection efforts where they are needed the most.
- The Policy Rules Triggered report provides information about which specific rules have been triggered and how many times. This information can help you understand which data handling practices are causing the most policy hits and may need to be addressed.
By regularly reviewing and analyzing these reports, you can constantly improve your data protection efforts and ensure that your DLP policies are effectively mitigating risks associated with data loss or exposure.
Step #7: Improvise Microsoft Office 365 DLP policies
To enhance the effectiveness of Microsoft Office 365 DLP policies in your organization, regularly revisit and revise your policies to ensure they remain relevant as your business processes and data protection needs evolve. Changes in data usage patterns, business operations, or regulatory requirements may necessitate policy updates.
Second, implement role-based access controls (RBAC) to minimize unnecessary exposure of sensitive data. With RBAC, you can ensure that employees only have access to data necessary for their job functions, thereby reducing the risk of data leaks.
Third, consider deploying a hybrid data protection strategy that combines the capabilities of Microsoft 365 DLP with other data protection solutions. This can help you extend data protection to non-Microsoft data sources and provide additional layers of security.
Lastly, integrate your DLP policies with other security measures like multi-factor authentication and encryption to create a robust, multi-layered defense against data breaches. Remember, the more holistic and integrated your data protection strategy, the better equipped you will be to prevent, detect, and respond to potential threats to your sensitive data.
Limitations of Microsoft 365 DLP
While Microsoft 365 Data Loss Prevention (DLP) provides impressive capabilities for protecting sensitive data in a Microsoft environment, it does have some limitations.
Firstly, its functionality is restricted to Microsoft 365 applications, which may not cover all data sources in an enterprise. This may necessitate additional solutions to protect data in non-Microsoft applications or databases.
Secondly, although Microsoft 365 DLP provides a range of predefined templates, customizing these to address the unique data protection needs of an organization can be complex and time-consuming.
Thirdly, Microsoft 365 DLP is dependent on network connectivity. If the network is down, policies may not be applied immediately, leading to potential data exposure. Most crucially, it cannot protect you from accidental deletion, malicious corruption, phishing attacks, ransomware and/or malware breaches. it does not replace the need for a comprehensive backup solution, as it does not provide protection against data loss due to issues at your end.
100% DLP with CloudAlly
CloudAlly’s top-rated Microsoft 365 Backup and 1-click recovery secures all your Microsoft 365 data from loss – Mail, Calendar, Contacts, Tasks, Groups/ Teams, OneDrive, SharePoint, and Public Folders.
With AWS S3 backups, built-in MFA, your choice of 8+ global data centers, unlimited point-in-time recovery and HIPAA/GDPR compliance, we tick all the checkboxes for secure, reliable and proven M365 SaaS data protection. Get 100% Microsoft Office 365 data loss prevention and never face M365 data loss again. Try us now – Start a Free 14-day Trial (No credit card | All Features)